In today’s work and live anywhere world, the global shift to remote work and the unprecedented use of personal devices have underscored the need for a truly secure BYOD network.
Until now, there have been two major concerns limiting widespread BYOD adoption:
- Companies desire to keep unauthorized devices from accessing corporate resources for fear of breaches to their private enterprise networks or loss of sensitive enterprise data.
- End users anxiety over the possibility of their company accessing, deleting, or worse, leaking their private information from their personal devices.
Enter Q-Scout – The First BYOD Privacy-Based Security Solution of Its Kind
At Quokka, we believe personal privacy and mobile security should live in harmony. And we’re making it happen with Q-Scout. Our Q-Scout solution provides intelligent, proactive security to safeguard you, your company and all of its employees, with privacy at its core.
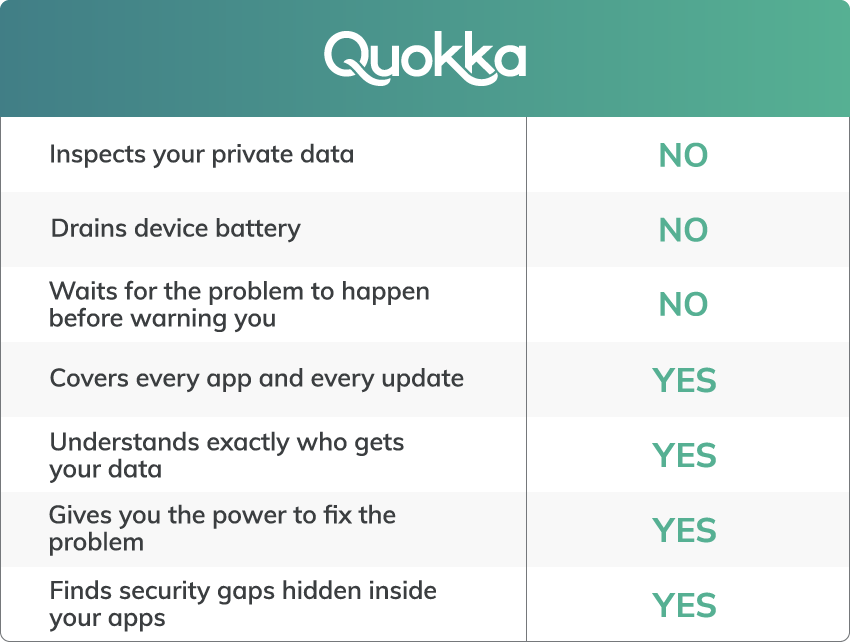
Q-Scout looks for and identifies security and privacy risks on devices by validating them for vulnerabilities, behavioral and policy/compliance failures – in the cloud, without taxing the device’s performance or battery. The end user is alerted to any security or privacy risks, with easy-to-follow steps to remove or reduce those risks. If a device is found to be non-compliant with corporate security policies, an alert is sent to the end user with clear instructions to fix the issue. At the same time, a simple message is sent to the enterprise portal so that the risky device can be blocked from accessing corporate resources. And the best thing – it’s all done with zero intrusion into the end user’s personal privacy.
How Q-Scout Works
Q-Scout consists of 3 main components
- The Mobile App installed on an Android or iOS device informs end users about the security and privacy risks on their devices with the intelligence and ability to remediate these risks before anything bad happens.
- The Enterprise Portal for administrators allows the enterprise’s IT or Security team to create, manage and enforce corporate security policies, alert end users about non-compliance and policy/behavioral failures, and oversee the security posture of the entire fleet of devices, and integrates with other enterprise solutions such as MDMs and IdPs
- The Security and Data Broker analyzes all of the mobile devices in the enterprise fleet and the apps on those devices, communicates with the end user devices and the enterprise portal, keeps end user personal information private, alerts the enterprise of at-risk devices, and maintains an inventory of the risks and compliance.
How Q-Scout Stands Out
Embraces Proactive Protection
Through the Enterprise Portal, administrators can create, manage and enforce corporate security policies 24/7, without accessing the end user’s personal, private data. Automatic enforcement of security policies minimizes false positives and avoids sending unnecessary security alerts to the IT or Security Team.
End users are given detailed information about the security and privacy posture of their devices and if necessary, how to remediate any issues found. Device owners always have complete control over their own devices.
Personal Privacy Guaranteed
Q-Scout drastically minimizes, if not eliminates, the need to manage multiple devices. It preserves end user privacy by validating the device without accessing user private data. End users can be assured that their private data is untouched and left intact. Moreover, companies can stay in line with industry privacy standards like GDPR or HIPAA and avoid any liabilities associated with accessing user’s private data.
Saves Companies Money and Resources
Systems like MDM’s are effective tools for managing remote devices in the work and live anywhere world. Unfortunately, these systems can be costly and require knowledgeable, experienced staff to maintain control over the company’s fleet of devices. Add in unmanaged (aka BYOD) devices and those systems fall short of their purpose. Ultimately, our solution eliminates the need for company-owned and controlled devices, saving your organization money and setting it up for a truly secure, effective BYOD, hybrid-working world.
The Q-Scout Difference